BrickStor
Security Platform
Passive backup strategies cannot defend unstructured data from theft or corruption
Minimize your threat exposure window with active cyber defense against ransomware, insider threats, and data extortion
The industry's leading cyberstorage solution
Data security delivered through data storage
RackTop’s BrickStor Security Platform (SP) is the first end-to-end cyberstorage solution with active security to detect and stop live ransomware attacks, insider threats, and data breaches in real-time. A data security platform for unstructured data, the solution supports presenting data to clients using standard NAS based protocols.
Our strong storage heritage with modern security delivers:
- Security
- Simplicity
- Savings
BrickStor SP can perform with security and compliance enabled at the pace of business and mission operations. Designed with a modern architecture to meet the most demanding workloads with scalable performance and capacity – from small datasets to Petabytes. The solution can be deployed on hybrid or all flash capacity to meet high IOPS, high throughput, and low latency access requirements.
Explore Features
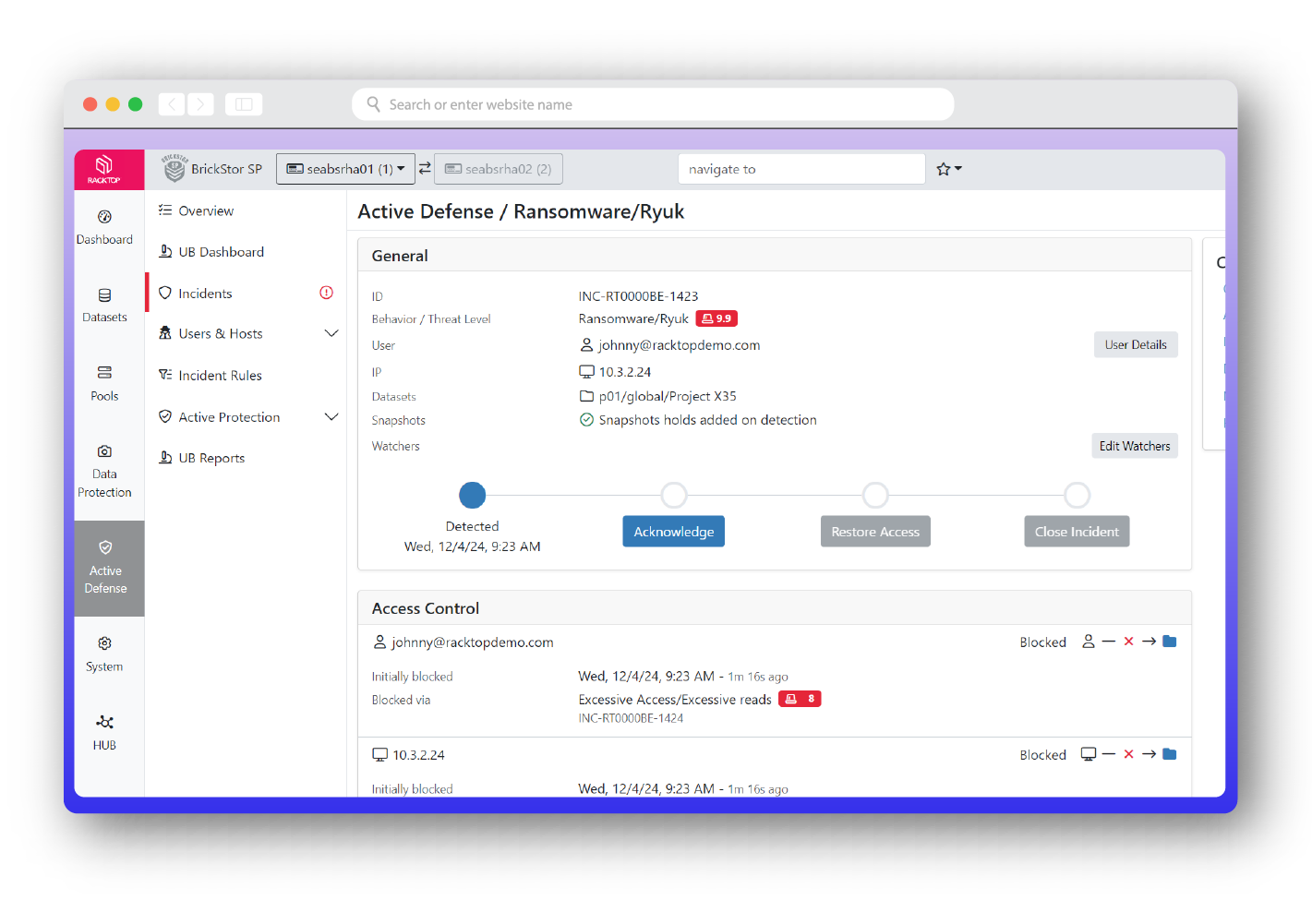
Active Defense
Stop ransomware and data theft in real-time with Cyberstorage. BrickStor SP actively defends SMB and NFS file shares, ensuring your most valuable data assets are protected from sabotage, ransomware attacks, and malicious insiders. BrickStor SP’s active defense features combine UEBA (user and entity behavior analysis) and SOAR (security orchestration automation and response) capabilities which are uniquely designed, engineered, and integrated to detect and stop data threats. Available as a drop-in replacement to your existing NAS (network attached storage), BrickStor SP can deploy as a virtual machine, on dedicated hardware, in the cloud, as a gateway to your S3 compatible storage, or on top of a SAN (storage area network).
User Behavior File Analysis
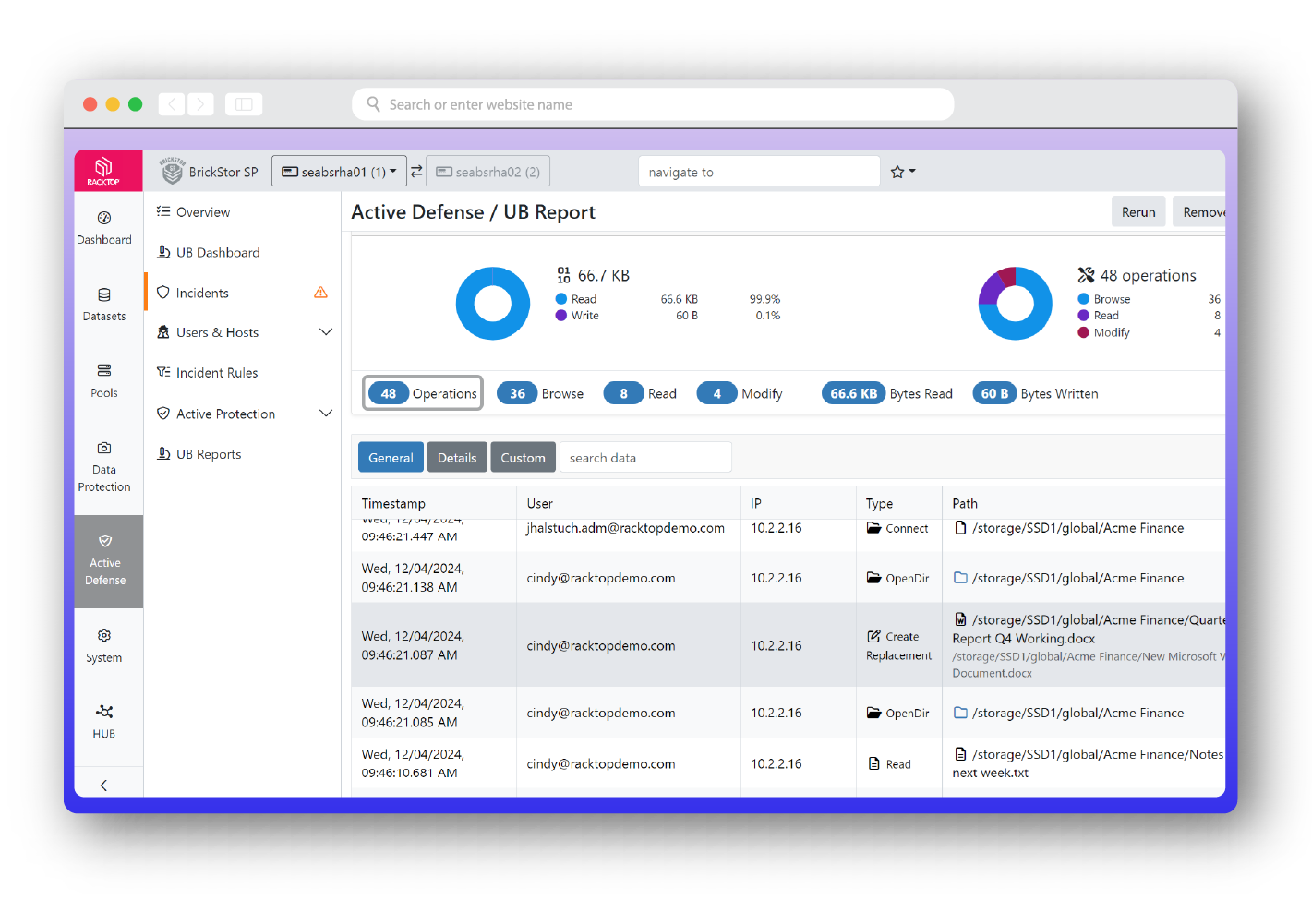
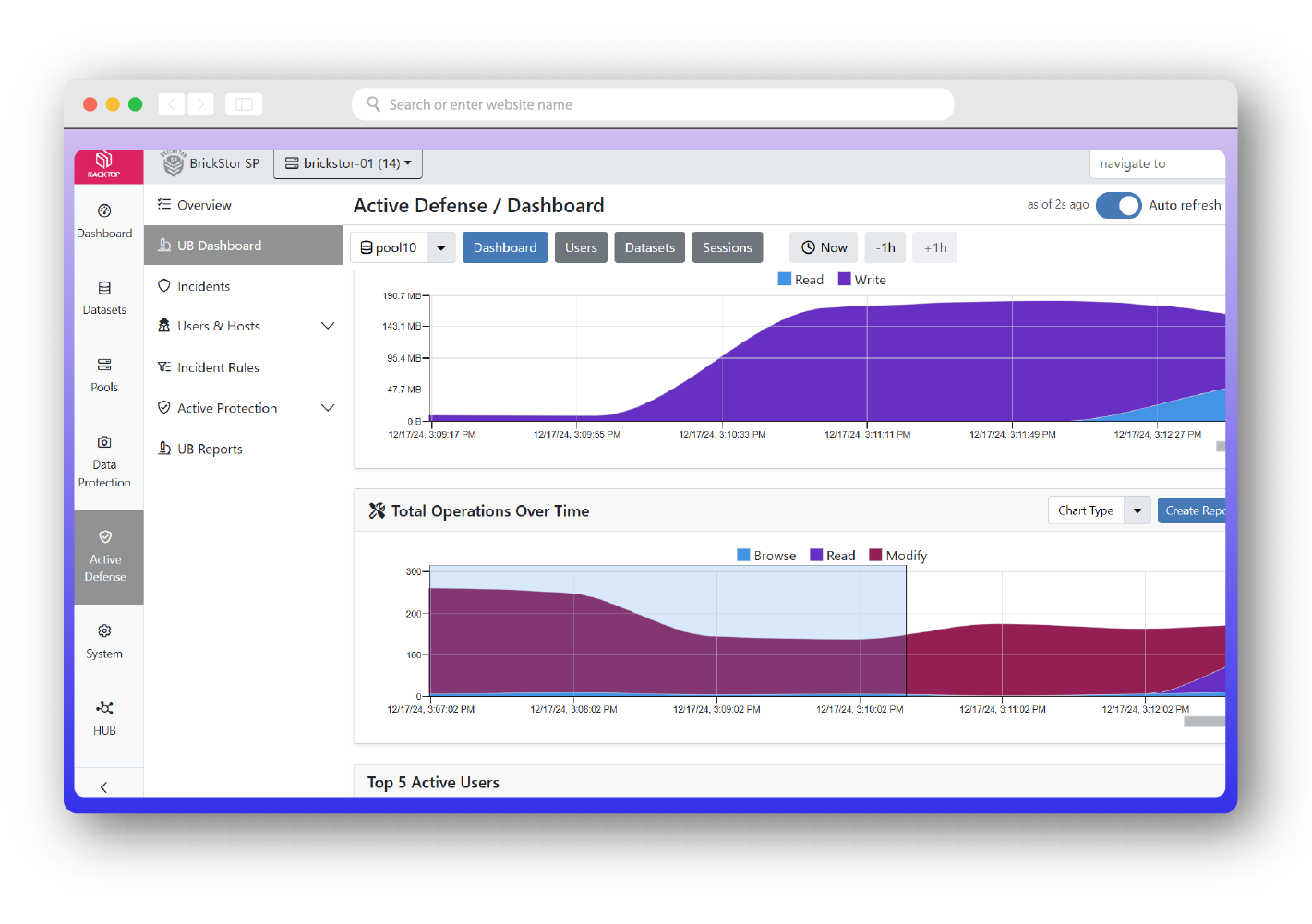
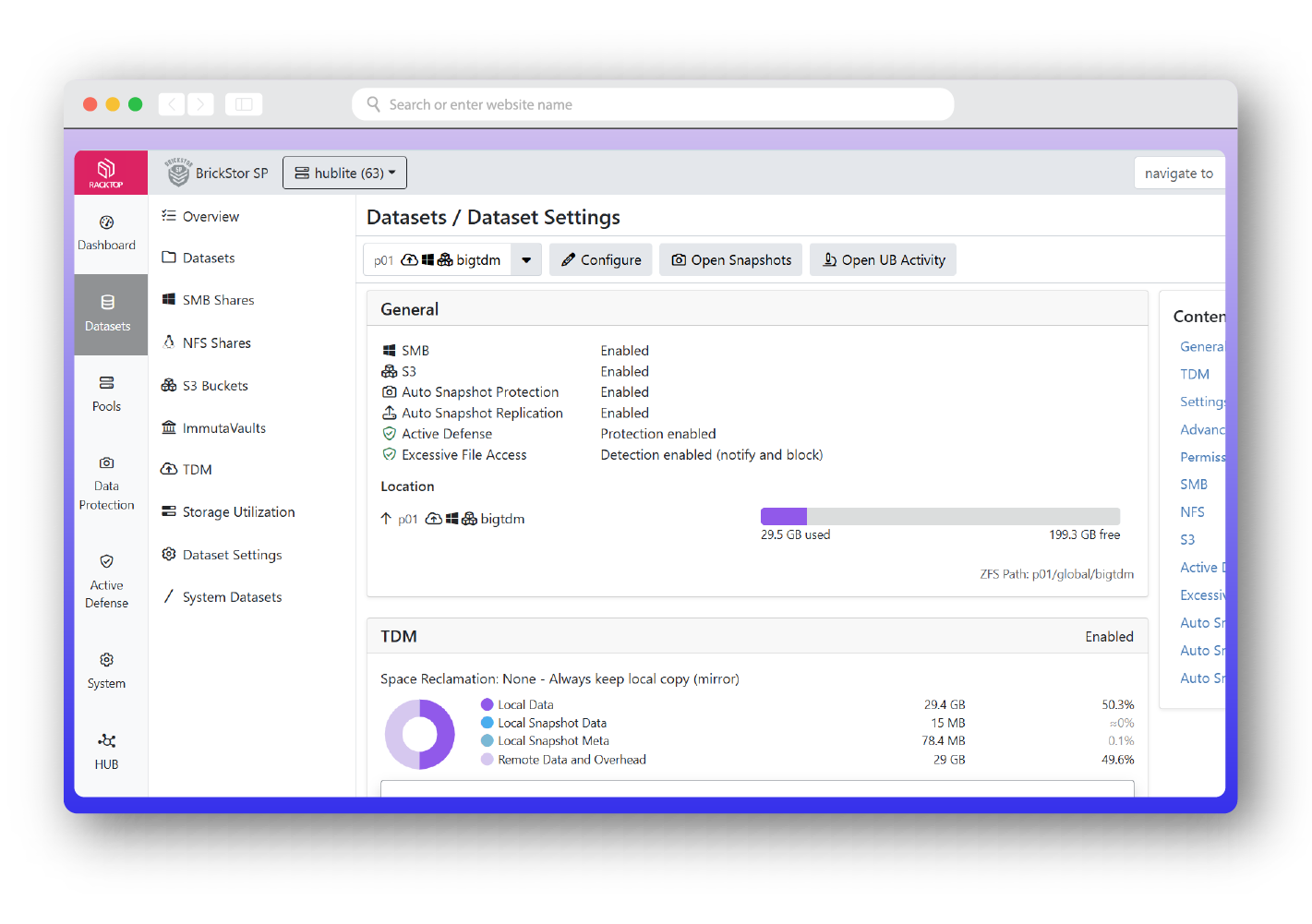
BrickStor SP was designed not only to protect against the traditional cyber attacker, but also to detect insider threats – the hardest attacker to detect and defend against. The profiling and analysis capabilities of BrickStor SP allows organizations to quickly and easily highlight anomalous and malicious behaviors through a high-performance proprietary search and analysis engine. Security officers can filter by time of day, path, protocol, client IP range, and more. BrickStor SP’s user behavior analytics (UBA) give stakeholders the highest fidelity information about their user’s behavior pertaining to their critical data. UBA allows security analysts and officers to see the entire life cycle of a file from the time it is created to the time it is cryptographically erased.
Metadata Intelligence
Know everything about your organization’s data all of the time. BrickStor SP collects and indexes vast amounts of data about each file including whether the data is local, in snapshots, or replicated to other systems that are under the management of BrickStor. Analysis engines transform that data into actionable intelligence that’s used to reduce risk and exposure, meet regulatory compliance, and identify previously undetectable security issues without any human intervention.
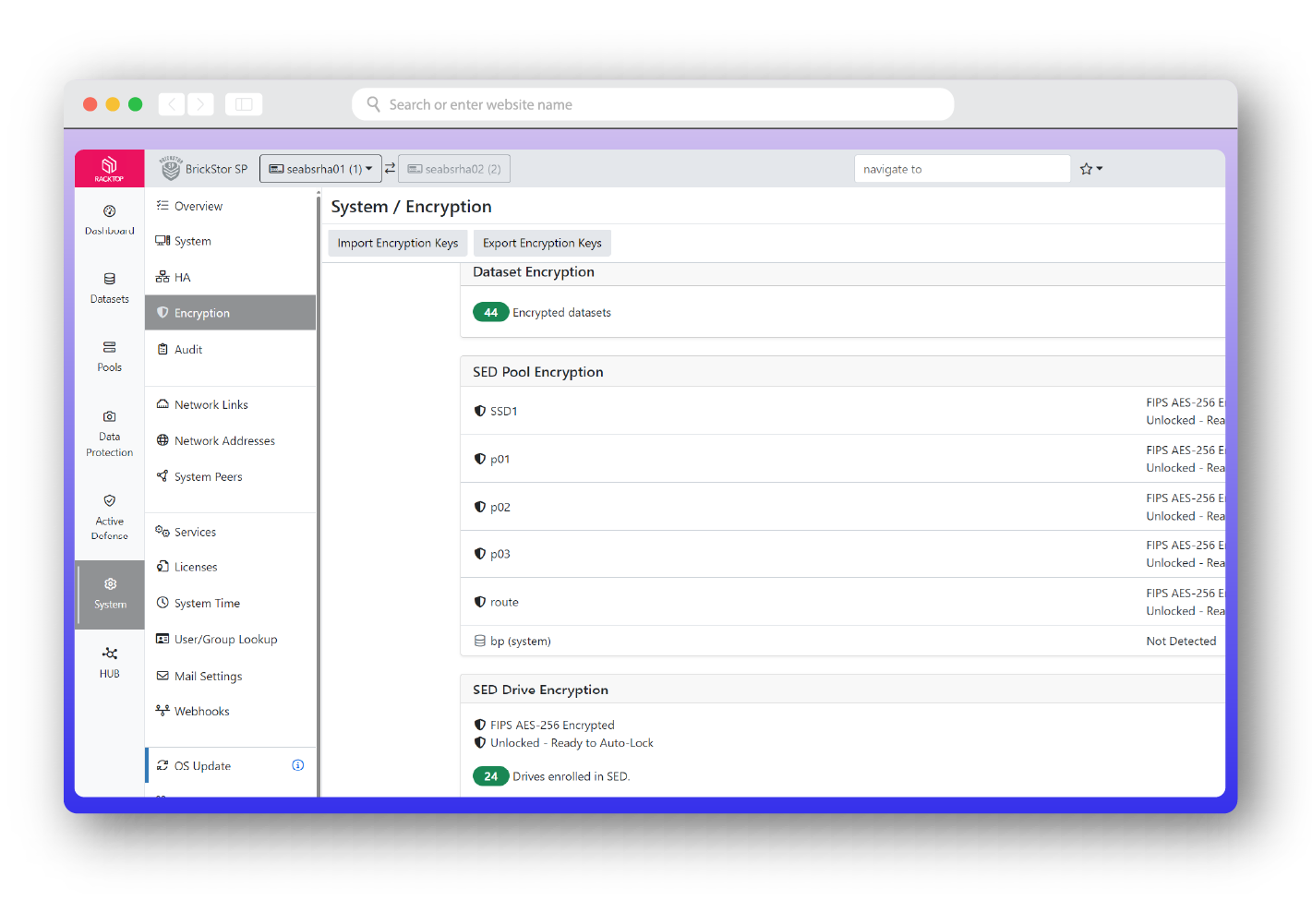
Encryption
FIPS AES-256 to manage keys without additional products. Encryption is the foundation of data security. BrickStor SP encrypts data twice – at both the physical and logical layers – with little to no performance impact using two separate keys. This process ensures your secrets are safe for centuries to come. Our KMIP-compliant security framework doesn’t require external key managers and it supports policy-based key rotation as well as auditing.
Transparent Data Movement
Seamlessly move data without disruption. BrickStor’s exclusive feature, Transparent Data Movement (TDM), enables the movement of data between file and object storage on premises and in the cloud to create economic efficiencies without disruption. TDM acts as a gateway to remote files, and can track user behavior and audit activity even though the data exists on a completely different storage system.
Integrated Compliance Reporting
Simple automated reports ensure your organization remains in compliance.
- CMMC
- GDPR
- HIPAA
- NIST
- SEC 17-A
- SOX
Utility Storage Features
BrickStor SP simplifies continuous compliance by enabling users to set policies and controls on the data. Protect data to the client with AES-256 encryption via encrypted SMB or NFS krb5p. Audits and compliance require an organization to explain how they deploy the controls and demonstrate control compliance through a body of evidence. BrickStor SP is designed to meet these controls and provide exportable and immutable evidence, such as logs or daily reports. Three primary examples of these standards include: data encryption for data security; privileged access management; and data protection policies for data retention.
Protocols and Namespace
| File Protocols | SMB 2 / 3 / 3.1.1, NFS 3 / 4 / 4.1 / 4.2 / S3 |
| Block Protocols | ISCSI, Fibre Channel 8 / 16 / 32 |
| Single Namespace | Microsoft DFS and NFS 4.1 |
Free 90-Day Subscription to BrickStor SP with RackTop's Jumpstart Program
Try Cyberstorage on your existing infrastructure today. Identify, protect, detect, respond, and recover from cyber attacks in real time.
Contact
Phone: +1 443-276-6973
Email: RackTop info
Support: Customer log-in
Address: 8170 Maple Lawn Blvd. Ste. 180
Fulton, MD 20759 USA
Request a demo